Explore & Discover: Hidden Gems & Twitter Insights - Plus More!
Are you tired of the relentless echo chamber of social media, craving a way to explore the digital landscape without the constant pressure of likes, follows, and public profiles? Discovering the hidden corners of the internet can be liberating, offering a unique perspective on trends, profiles, and data that transcends the conventional social media experience.
The digital world offers a complex tapestry of information, and navigating it effectively requires the right tools. One such tool is Sotwe.com, a platform that allows you to browse Twitter anonymously, eliminating the need for a login. This is particularly beneficial for those who value privacy or live in regions where Twitter access is restricted. Launched around 2015, Sotwe caters to users seeking to explore tweets, profiles, and trends without the commitment of signing up for an account. It is a way to interact with social media on your terms.
| Feature | Description | Benefit |
|---|---|---|
| Anonymous Twitter Browsing | Access tweets, profiles, and trends without logging in. | Maintains privacy, bypasses location-based restrictions. |
| Historical Trend Tracking | Keeps track of trends for various countries. | Allows users to stay informed on trending topics. |
| Accessibility | Provides access to Twitter content without an account. | Lowers entry barriers, facilitates trend exploration. |
Sotwe.com Official Website
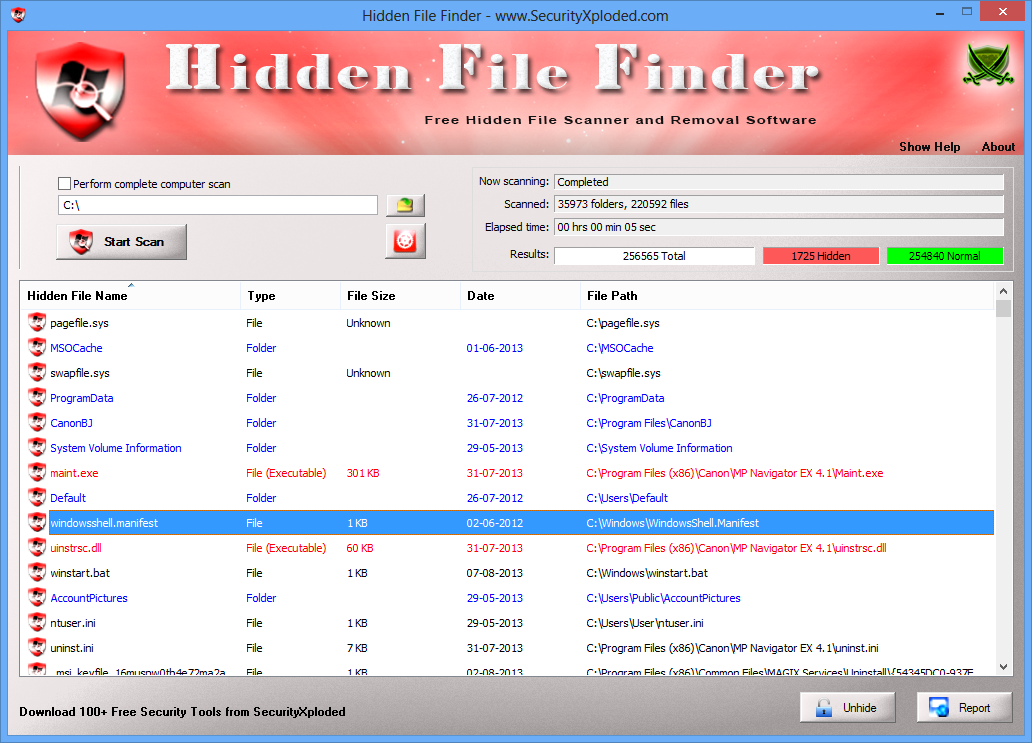
Beyond the realm of social media, the digital landscape encompasses a multitude of hidden aspects, from obscured files on your computer to sensitive data residing on your devices. Hidden File Finder emerges as a valuable tool in this context, acting as a free software solution for swiftly scanning and uncovering concealed files within your Windows system. This software conducts a rapid, multi-threaded scan of all folders, efficiently unveiling hidden files that might otherwise remain unnoticed. Understanding that some files and programs are purposefully concealed is a crucial first step.
The presence of concealed elements extends further into the operational mechanisms of your computer. Background processes and applications that launch upon startup are often hidden from direct view. While many of these processes serve legitimate purposes, such as enabling applications to run efficiently, some may be malicious, potentially slowing down your system or compromising your data. The ability to understand these background processes becomes critical for maintaining the security and speed of your digital environment. The control panel and app settings in Windows 10 are common locations to search for installed apps, even if some are hidden.
In the face of potential threats, the importance of safeguarding your devices and securing your data cannot be overstated. Numerous apps and services, such as "hiddenapp," are designed to provide a robust layer of security. Offering features like track & locate, remote locking, and data wiping, these tools empower users to protect their sensitive information. It's important to be aware that not all programs are displayed on your computer's taskbar and that some programs continue to run in the background, even after being closed. This underscores the need for constant vigilance and the utilization of appropriate security measures.
For those seeking a deeper dive into the world of Twitter profiles, platforms like Foller offer comprehensive public profile analytics. By simply entering a username, users can gain insights into a profile's location, language preference, joining date, profile URL, follower statistics, and engagement metrics. Foller provides a detailed view, from the most linked domains to the user's twitter activity time. Subscriptions often unlock advanced features, and it's best to check current pricing and subscription options.
Similarly, tools like mSpy emphasize the importance of proactive knowledge. By providing users with comprehensive insights into their devices' activities, mSpy aims to empower users and promote responsible digital habits. While the core functionality of these tools often centers on monitoring and analysis, it's essential to use them ethically and in compliance with privacy laws. It is also important to be aware of the latest software, games, programs, and apps, keeping your devices updated for improved performance and security.
| Topic | Description | Relevance |
|---|---|---|
| Stalkerware | Software installed on devices to monitor activity. | A serious privacy threat; can monitor calls, texts, and location. |
| Hidden Processes | Background services and applications that run automatically. | Some may be malicious; can slow down your system or compromise data. |
| Device Security | Tools to protect devices and data (e.g., track & locate, remote locking). | Essential for keeping your devices and data safe. |
Example Security Website
While navigating the internet's depths, it is important to remember that many sites and content creators may not allow descriptions. Some individuals and communities prefer anonymity or wish to showcase their work without being directly linked to platforms or search engines. Consider the digital artist and their gallery, where breathplay, drowning, and themes related to water are frequently featured. Also, consider the video content, from model casting to adult films. Due to their nature, these works might be presented without a description or be designed to be viewed in the private online communities.
The digital world offers a vast array of experiences, ranging from anonymous browsing on social media to software for recovering lost data, and digital artist to content designed to be privately viewed. The key is to be aware of the tools available and how to use them responsibly while recognizing the existence of content that may not be readily accessible or described in detail.


Detail Author:
- Name : Nettie Ernser
- Email : jayde.stamm@mckenzie.org
- Birthdate : 1989-01-10
- Address : 7713 Johnston Rapids Apt. 148 East Rosamond, FL 37478-2972
- Phone : 1-458-844-1908
- Company : Rath-Gottlieb
- Job : System Administrator
- Bio : Perspiciatis omnis et sed aliquam et quo. Corrupti aut dolorum quia reiciendis quis. Maxime quae quis aut consequatur ab explicabo vero. Veritatis error tempora qui exercitationem odit.