AWS IoT Secure Tunneling: Remote Access & SSH Guide | [Tutorial]
Is it possible to remotely access and manage your IoT devices securely from anywhere in the world? The answer is a resounding yes, thanks to the innovative capabilities of AWS IoT Secure Tunneling. This powerful feature provides a robust solution for establishing secure, bidirectional communication with your remote devices over a secure connection managed by AWS IoT. This allows you to monitor, troubleshoot, and even update your devices without the need for complex firewall configurations or the challenges of traditional remote access methods.
AWS IoT device management offers a comprehensive suite of tools designed to facilitate the creation of IoT applications across a wide array of industries. While previously, remote access often involved sending control messages through MQTT topics or updating device shadows, Secure Tunneling presents a more streamlined and secure approach. It eliminates the need for complex firewall configurations by leveraging the security provided by AWS IoT, allowing you to maintain the same level of protection you would expect at a remote site. Whether you're looking to monitor device anomalies, take mitigating actions, or rectify device states, Secure Tunneling offers a straightforward solution.
| Category | Details |
|---|---|
| Concept | AWS IoT Secure Tunneling for remote access to devices. |
| Technical Details |
|
| Features |
|
| Benefits |
|
| Reference Website | AWS IoT Secure Tunneling Documentation |
The ability to remotely access devices is crucial in today's interconnected world. For instance, imagine a scenario where you need to connect to a remote device, named "remotedevice1." Using AWS IoT Secure Tunneling, whether you've used the manual setup or the AWS IoT API, the process becomes incredibly straightforward. This blog delves into using AWS IoT Secure Tunneling to create an SSH tunnel that connects a source, like your AWS environment, to a destination, such as your Macbook.
When setting up your "IoT device", the initial steps will often involve getting it connected and communicating with AWS IoT Core. This could involve using an AWS IoT device client or, for more complex scenarios, leveraging the capabilities of AWS IoT Greengrass. Upon the successful setup, you'll then want to verify that your device is sending data to AWS IoT Core. This initial validation ensures a solid foundation for subsequent steps.
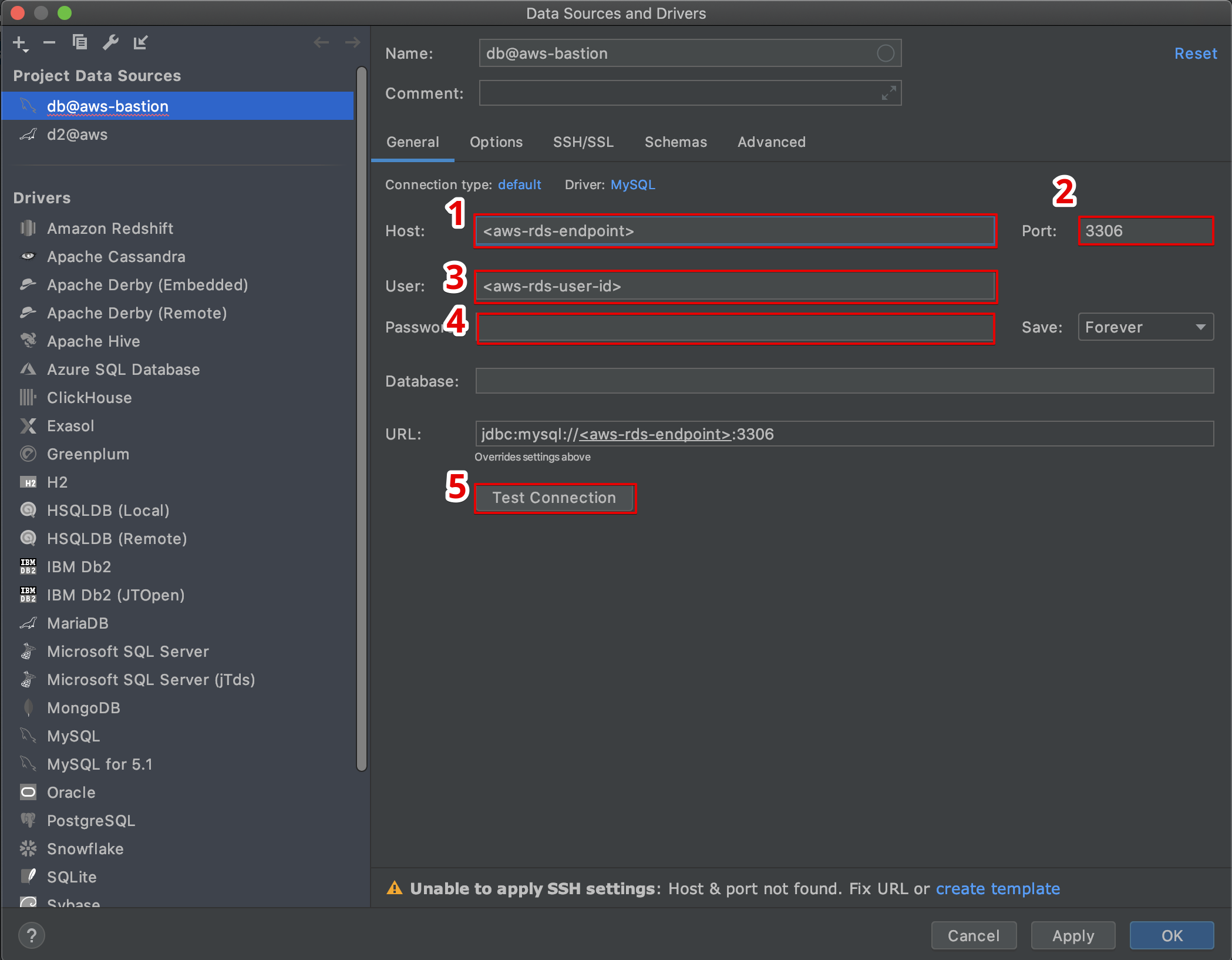
With the tunnel created using IoT Core, the access tokens for both the source and destination are generated. This is the moment to proceed by running local proxy, operating in "destination mode." After this, You can easily use the AWS Management Console's secure shell (SSH) to connect to your device and register it.
One of the compelling advantages of AWS IoT Secure Tunneling is its support for private key SSH authentication. This feature streamlines the process of monitoring device anomalies, enabling you to take swift mitigating actions and rectify device states as needed. Because of this, it reduces the need for manually setting up and handling device access tokens.
The method eliminates the need for a local proxy. Quick setup method can be used to route the access tokens and SSH from the browser to remote devices. In order to open a tunnel in this manner, an IoT thing (for example, remotedevicea) must already be created in the AWS IoT registry. For more details, consult the AWS IoT documentation on registering devices.
The creation of a tunnel is a streamlined process. You can create a tunnel from the tunnels hub page or the details page of the created IoT thing in the AWS IoT console. When creating a tunnel from the tunnels hub, you can specify whether to use the quick setup or manual setup method.
You can't edit the configuration information of an existing tunnel. Instead, use the quick setup method to get access tokens and SSH to the remote device. You must create an IoT thing in the AWS IoT registry (e.g., remotedevicea) to open a tunnel using this method. Consult the documentation on registering devices in the AWS IoT registry for more details. Also, after the tunnel is opened, the AWS IoT device management gives you the cat for the source that you can download on the source device. Use the cat to start the local proxy in source mode to connect the source side of the tunnel.
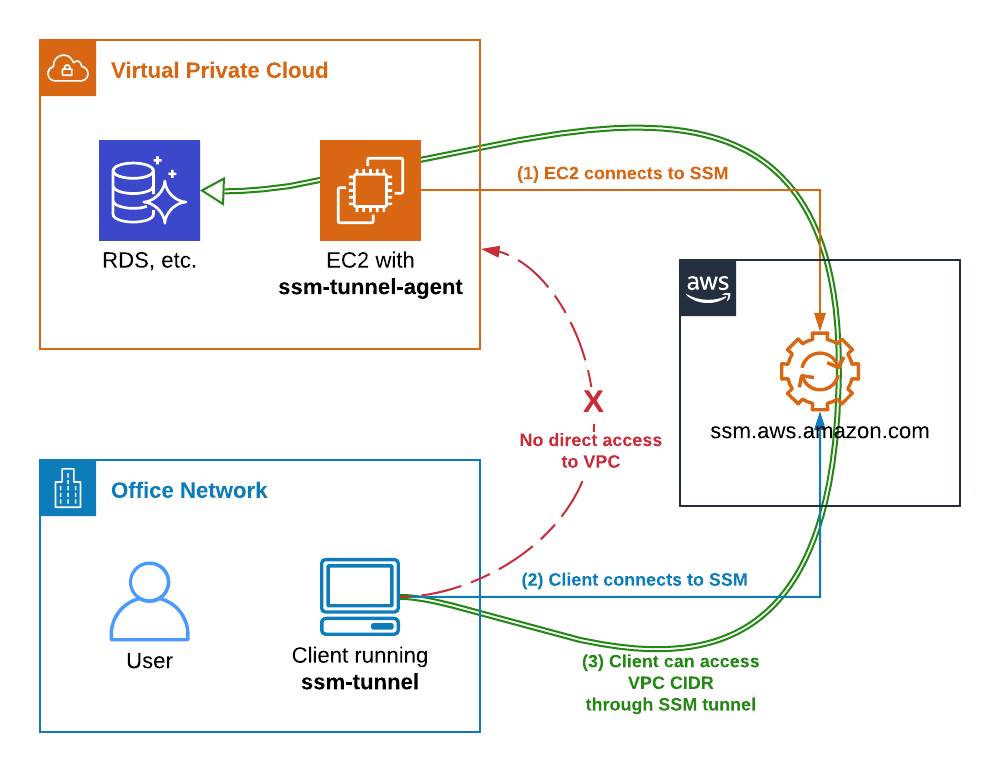
When utilizing AWS IoT Secure Tunneling, you are essentially creating a virtual pathway to your device. This managed tunnel simplifies the opening of an SSH connection. For detailed guidance on connecting to remote devices using AWS IoT Secure Tunneling, refer to the AWS IoT Developer Guide.
For a device to connect to AWS IoT, you would need an IoT device agent on the remote device connected to the AWS IoT device gateway. This would then listen for new tunnel notifications using MQTT and would be configured with MQTT topic subscriptions.
Moreover, Secure Tunneling is designed to integrate seamlessly with AWS IoT. This integration ensures that you can access your IoT devices remotely from any location, making device management far less cumbersome. One of the crucial aspects of security is to specify a timeout on the credentials. It's recommended to keep this value low so that if the access tokens are leaked, they will naturally expire. The process simplifies the devices onboarding, which eliminates the necessity of compiling and installing a local proxy on the operator's device.
There is also an option to specify a timeout on the credentials. I recommend keeping this low so that if your tokens get leaked somehow, they will naturally expire. You will start the local proxy (with destination mode) to use in conjunction with secure shell (SSH) in the AWS Management Console to connect and register the device.
Secure Tunneling also supports private key SSH authentication, simplifying the process of monitoring anomalies, taking corrective actions, and fixing the device's state. Additionally, you can create a virtual device with Amazon EC2 and start an ssh session.
In order to delete an individual tunnel or multiple tunnels from the AWS IoT console, go to the tunnels hub, choose the tunnels that you want to delete, and then choose delete tunnel. To delete an individual tunnel or multiple tunnels using the AWS IoT API reference API, use the closetunnel API operation.
Furthermore, to gain remote access to devices from a web application, you will learn how to use this AWS IoT device management feature. The process is simple; you can create a tunnel from the tunnels hub or the details page of the created IoT thing in the AWS IoT console.
By leveraging AWS IoT Secure Tunneling, businesses across every industry can build robust IoT applications. Unlike previous approaches which often required the customer to send control messages through an MQTT topic or update a device's shadow, Secure Tunneling offers a more secure and efficient solution, streamlining the remote access experience.
This guide teaches you how to use the quick setup method to open a tunnel from the tunnels hub page. It also teaches you how to access remote devices using browser-based SSH and the AWS IoT consoles command-line interface.

Detail Author:
- Name : Kaleb Hackett
- Email : jacky22@balistreri.com
- Birthdate : 1980-03-15
- Address : 16099 Wilford Rest North Demarcus, IL 71204-9953
- Phone : (307) 537-1783
- Company : Tromp, Dooley and Aufderhar
- Job : Transportation Equipment Painters
- Bio : Et et ut consequatur vel veniam et ipsa odio. Ab reiciendis dicta nihil rem quos. Provident qui perferendis qui itaque aperiam tempore.